Last year, American businesses lost over $3 billion due to business email compromise (BEC) scams. What is BEC and how do we protect ourselves?
By Andrew “AJ” Jarrett – Program Manager, CRC Technical Assistance
What is Business Email Compromise?
BEC scams are a highly targeted form of social engineering utilizing what appears to be a legitimate email to convince victims to transfer money or provide banking information to the threat actor. This might sound a lot like phishing, and indeed they are very similar, however the primary difference between phishing and business email compromise has to do with the level of targeting and sophistication.

BEC threat actors (aka the bad guys) will often use what appears to be a legitimate email address from someone the victim would expect to receive emails from. Threat actors use a multitude of methods to appear legitimate from spoofing a legitimate email address, setting up an email address and domain name that is very similar to the legitimate address, or by compromising a real email account.
Business email compromise threat actors typically do their homework before launching an attack. In many cases the threat actors will research the organization they are targeting and learn the names and contact information of employees within the organization that they might be able to scam as well as vendors that they work with. Due to open records laws, municipalities are especially vulnerable to this sort of attack as specific information such as the name of a contractor, the specific amount of the contract, and payment terms are typically public information once the project has started.
BEC is on the rise
According to the FBI’s Internet Crime Complaint Center, BEC has been steadily on the rise in the past few years. New campaigns are discovered daily targeting everything from small businesses and real estate to academic institutions and municipal governments.
Recent attacks in Texas include:
Harris County in September, Galveston County in June and the City of Bryan in March of last year totaling over $2 million! Combine that with numerous other unreported incidents with private businesses and you get a growing worldwide threat.
What does BEC look like?
Although methods vary, typically business email compromise attacks target specific people within an organization such as accounts payable or comptrollers with the authority to transfer money or make changes to vendor electronic payment methods.
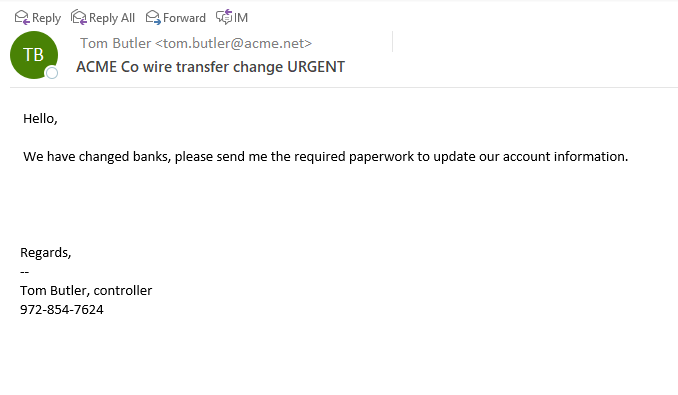
The attackers will typically impersonate a vendor or contractor and request to have their banking information changed. In many cases the emails will appear to come from someone familiar and may even replicate details such as the person’s email signature to appear more legitimate. In many cases, the attacker will create a sense of urgency, claiming that they might get in trouble with their supervisors if this isn’t handled immediately or that there is a big deadline that they are up against. In some, but not all cases, the attackers may not be native English speakers and so grammatical mistakes and miss spellings might be present. Some attackers hide their spelling issues by claiming to be sending the email from mobile (because who hasn’t miss-typed something on their phone before). It is important to pay close attention to details and become suspicious if a request comes through with one or more of these red flags.
How to defeat the bad guys
In most cases of business email compromise, the threat actors have worked hard to cover their tracks and make their requests seem legitimate. You should become suspicious if:
– The email contains multiple spelling and grammar mistakes
– There is a sense of urgency to the request
– The email address or domain name does not exactly match
– The email is originating from a generic account like “Administrator” or “Accounts Receivable”
Despite all this, there is always the chance that the email address is legitimate because they have hacked the email account of the vendor and mirrored previous correspondence to avoid suspicion. No matter what the case, the best way to prevent business email compromise is this:
Create a procedure within your organization to verify financial transactions and payment information using a second method, such as by phone before complying with any such request.

Also realize that Social Media is a huge source of information for scammers. Know who you’re connecting with and be mindful of what you are posting online. Details such as when you go on vacation can be used by BEC attackers to scam someone using your identity!
So, that’s all fine and good, but what if you catch the BEC too late? Fret not as there is some recourse if you catch it quickly. Law enforcement agencies such as the FBI can activate what is called the Financial Fraud Kill Chain to stop a wire transfer in it’s tracks. In addition, your bank may have some options for stopping checks and ACH transfers as well but remember; the longer it has been since the transaction, the harder it becomes to reverse. When in doubt, contact law enforcement and your bank immediately.
Like what you just read?
Check out cyberready.org for more great tips, training, and professional services to keep you cyber-ready!
